Tangent’s explosion-proof computers are robust and purpose-built for the oil and gas industry. In environments characterized by the presence of flammable or explosive vapors or gases, such as those found in the oil and gas industry, prioritizing safety and reliability is of utmost importance. Tangent’s commitment of manufacturing best-practice purpose-built computers has heard the demands […]
Month: February 2024

DMARC Director Can Save Your Organization Millions
According to the latest Forbes article, “The Underestimated Scourge of Spoofing Attacks” “dwell time” for cyberattacks shrunk to 8 days in 2023, compared to 10 days in 2022. Dwell time refers to the time from when a cyberattack starts to when it has been detected. While shrinking cyberattack detection times is good news, an 8 […]
Software Licensing Compliance Tool
Software License Management (SLM) involves centrally managing software licenses across an organization. A software license is a legal document issued by publishers or distributors, outlining rules for software usage. The SLM system, a subset of software asset management, includes tracking, documenting, and controlling software usage. It aids in compliance with end-user license agreements (EULA), notifying […]
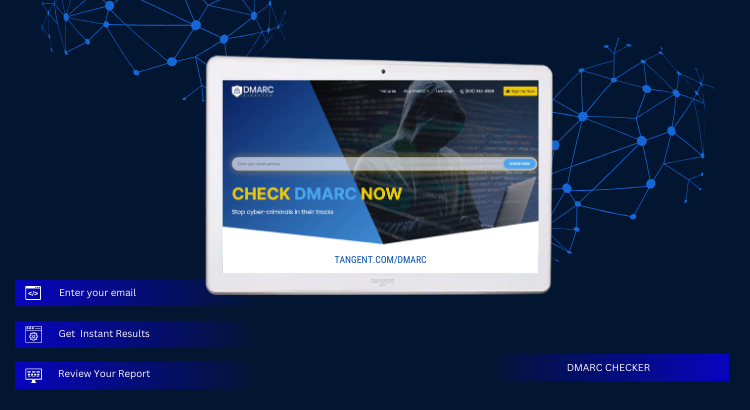
Test DMARC with Our Easy-to-Use DMARC Checker
Head over to Tangent.com/DMARC to check DMARC. Receive comprehensive, easy to understand results. Test DMARC quickly and accurately by entering your domain. Our DMARC checker is free and easy to use, no registration or personal information required. DMARC protocols properly configured help prevent spammers, hackers and spoofers from jeopardizing your company. Secure your finances, sensitive […]

Medical PCs That Make Work Easier
Medical PCs play a crucial role in making work life easier for nurses by providing tools and features tailored to their needs in healthcare settings. How Medical PCs Benefit Nurses: Streamlined Documentation: Medical PCs allow nurses to efficiently document patient information, including vital signs, medications administered, and treatment plans, directly into electronic health records (EHR) […]
